saXon offers a complete portfolio of cyber security services designed to assist organizations in assessing, measuring, analyzing, and resolving information security vulnerabilities.
Our comprehensive, in-depth assessment services identify major risk areas within an organization’s network and environmental infrastructure. Drawing on years of real-world operational experience, we provide clients with actionable intelligence, sound strategies, and robust protection.
As enterprise networks are becoming increasingly more open, they are more exposed to threat.
Having an integrated enterprise-wide network security solution is pivotal for securing your enterprise data and keeping your business up and running.
IT security and risk mitigation is a significant challenge for organizations. An increasingly mobile workforce, collaboration across organizations, compliance requirements and the evolving security threat make managing IT security highly complex.
saXon help you with a consistent approach for securing your network infrastructure, implementing new technologies, accommodating new users, improving network performance and security, and reducing cost of operations.
- Network Security Architecture Design and Implementation
-
Computer Network Defense (CND)
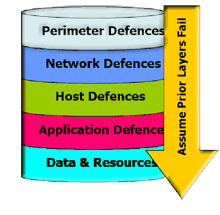
- Computer Network Operations (CNO)
- Secure Remote Access
- Network Access/Admission Control
- Network Intrusion Detection/ Protection
- Virtualization Security
- DDOS mitigation
- Security Configuration Assessment
- Security Training
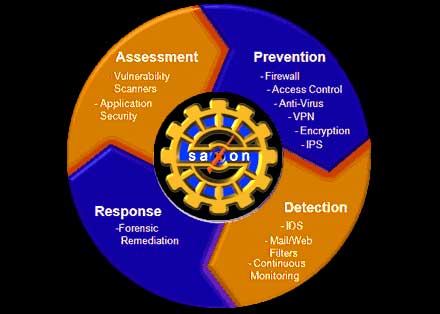
Our Engineers have real world operational experience designing secure networks for both government and commercial enterprises. We continuously refines our approach to security problems. Hence we deliver the right solution tailo
red to the customer’s specific needs.











